Everybody’s environment is hybrid these days.
With the democratization of virtualized services, no company is entirely on-premise anymore (or 100% cloud for that matter). If you use SaaS applications like Gmail, Dropbox, Office 365, Google Docs, or Salesforce, then you are relying, to some degree, on public cloud infrastructure to conduct your business in congruence with your on-premise environments.
Every modern company is a mixture of physical, private, and public. And while hybrid cloud has made IT much more efficient and cost-effective in recent years, it has also posed considerable difficulty for IT teams to secure and protect their external workloads efficiently. With the increasing pressure and sophistication of modern cloud security threats, your cyber defenses have to become a priority. Each component of your hybrid environment requires a different security technology and set of protocols to secure—it’s up to you to find the right mix of backup and security to make this happen.
To help you establish your own best practices, Corey Gary, Enterprise Solutions Architect at Technical & Scientific Application, Inc. shares his insights on how to establish comprehensive and scalable hybrid cloud protection.
The Reality of External Workloads and Cloud Services
It’s important to remember that you protect hybrid cloud the same way that you protect your on-premise infrastructure; only now you need to accomplish similar ideas with different methods.
While most cloud platforms provide scalability and redundancy—with SLAs that guarantee infrastructure uptime—they do not provide protection for your data and applications. You receive no data security (except for what happens to protect the cloud provider’s infrastructure).
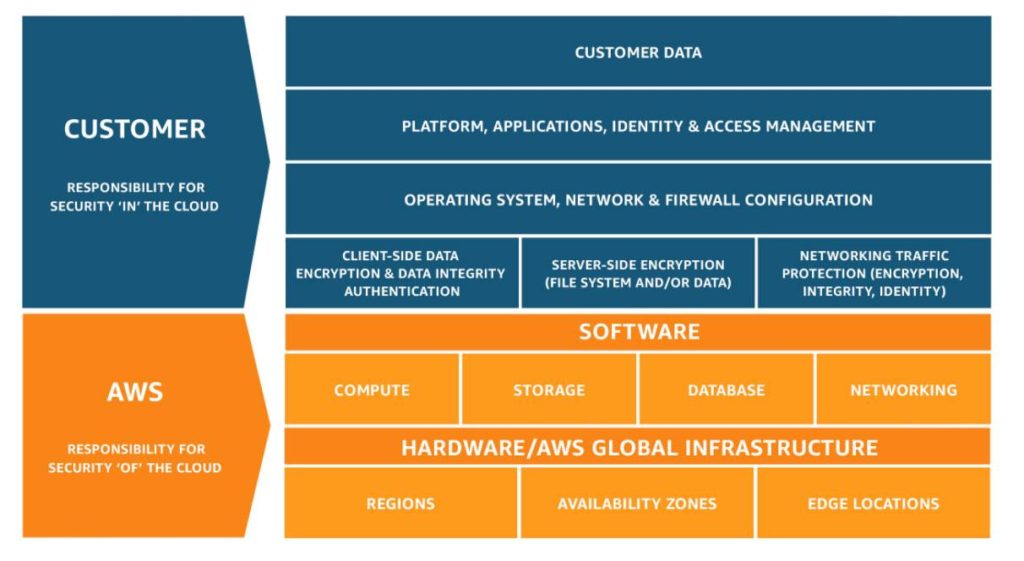
As you can see from the AWS Shared Responsibility graphic above, It’s up to you to construct that protection and redundancy for your environment.
Backup and Archiving
How do you make copies of your data?
With hybrid cloud, the “rule of three” (also known as Backup 3-2-1) still applies:
- 3 Copies of your SaaS data (Active, Redundant, Archive)
- 2 Different Storage Devices or Targets (local disk, cloud disk)
- 1 Offsite backup entirely separate from your on-premise and cloud environments
Office 365 does not provide backup services, so you need to use tools like Veeam Backup or Barracuda Essentials to prevent data loss with cloud-based backup and archiving for your data. If you leverage AWS for any of your workloads, then, for example, you should create redundancy across environments by replicating that data to Azure and vice versa. Cover your [cloud] bases because you want to have access to every data store even if disaster eliminates one of them.
Threat Scanning – Defending Against Hybrid Cloud Security Threats
Spam and Phishing Attacks
Are you conducting threat scanning across all of your environments? Are you still checking the edge and access security?
Cloud increases your attack surfaces. Consider what you need to do to add security to your Dropbox, Box, or Salesforce platform. These SaaS offerings are encrypted, but threats remain. You will need to acquire a decryption key from each to establish your own tool for monitoring and threat response. Use a security tool like Prisma SaaS from Palo Alto that gives you insight into your specific area within the service, allowing you to scan all of your files actively for threats. Moreover, Barracuda Essentials doesn’t just offer backup and archiving; it also provides spam, phishing, and data theft prevention through advanced threat detection. For added protection, tools like Azure Sentinel can layer over your threat detection tools to provide machine learning-driven SIEM services and heuristic threat intelligence.
Gateway Security
What about edge security?
You have always had to protect your network from cyber attacks (since the mid-1990s at least). But now, you have to extend that protection into the dark grey box of cloud. If you have workloads hosted in public clouds like Azure, AWS, or Google, you need to deploy a virtual firewall to protect all of your cloud instances and workloads. Next-generation Cloud App Security Broker (CASB) solutions, like those from Palo Alto, Check Point, and McAfee, allow you to gain visibility into everything that the XaaS provisions as well as providing intelligent measures like credential phishing protection. It’s also important to consider that firewall solutions are stronger if you use the same vendor on both ends—allowing you to maintain your established security practices and often, your configurations, between environments.
Access Security
Do you have user access and role-based access control for your external workloads?
These CASB solutions also provide scalable access management to control who can gain access to which cloud platforms and when. Tools like these help you to enforce password protocols more strictly than before (e.g., you can set password refreshes, deny reuse of AD credentials, etc.). They also include more robust machine learning-based protections to prevent account hijacking or data breaches caused by human error and mishandled identity credentials.
Experience Under Fire
“We were Technical & Scientific Application, Inc. long before the Transportation Security Administration was established,” explains Corey Gary, “Our identical acronyms and similar domain names sufficiently confuse would-be hackers. They don’t discriminate between the ‘.com’ and the ‘.gov,’ so we get attacked with the same aggression and strength that government sites experience.”
When Corey was first looking at the different security vendors available on the market, he found that “each one was immediately put through its paces [when brought in for PoCs at TSA]. If any company environment is going to get hit, it’s going to be the government. And our current security posture is keeping us defended from attacks meant for our government namesakes, so the technologies that we implement come highly vetted.”
Corey continues, “Normal people are still getting hit; it’s not just the government sites. And proper security is all a matter of how much insight you have into your environments and how you decide to implement the proper measures to defend them.”

